Overview
Last updated August 6th, 2025
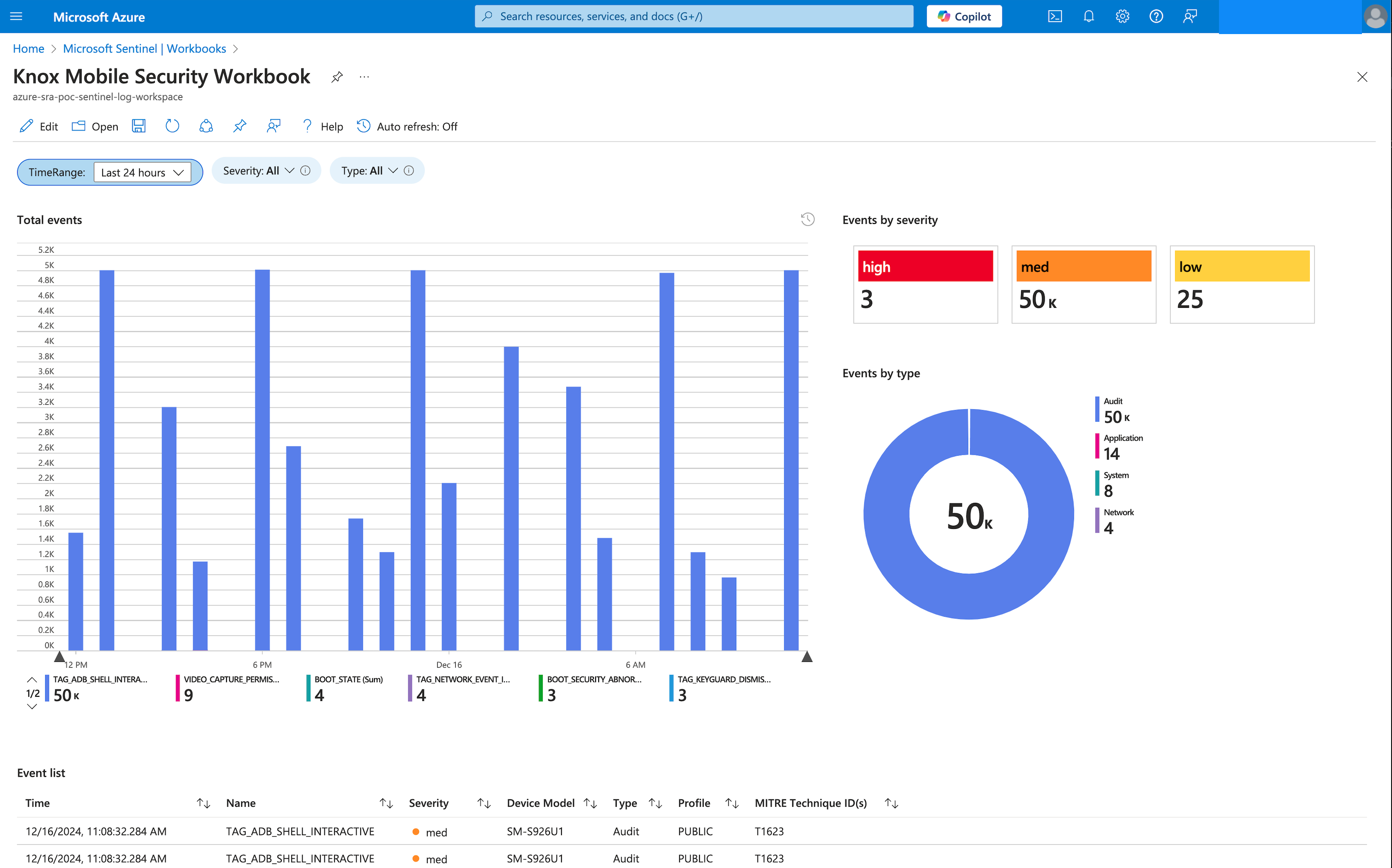
The Samsung Knox Asset Intelligence for Sentinel solution provides enterprise IT admins and SecOps (security operations) teams with the ability to capture security telemetry data from Samsung Galaxy devices, and have that data converted into events and logs in Microsoft Sentinel.
Once this solution is deployed in Sentinel, IT and security administrators can configure on-device Security Logs to send security threat alerts directly to their Security Operations Center (SOC). This allows SOC analysts and enterprise security teams to view and manage these alerts and prompting effective triage, incident identification, and response efforts.
Prerequisites
To use this solution, you’ll need to have the following from Samsung Knox and Microsoft Sentinel:
Samsung Knox
- A Samsung Knox account. For more information, refer to Create a Samsung account.
- A valid Knox Suite license, or a Knox Asset Intelligence license.
- Samsung Galaxy devices running Android 15 or later, and an appropriate Knox version. See the Devices secured by Knox page for more information.
- Devices configured as either fully managed, or as company-owned with a work profile. For company-owned devices with a work profile, the Knox Asset Intelligence agent must be installed in the work profile in order to enroll. See Enroll devices for more information.
Microsoft Azure
You’ll need to pre-configure several services in your Azure portal, including Microsoft Sentinel, Log Analytics workspaces, Microsoft Entra ID before proceeding with this integration. The following Azure services or resources are required:
- An active Azure subscription
- An Azure Resource Group created.
- A Log Analytics Workspace instance created and deployed.
- A Microsoft Sentinel instance created and deployed with the following Sentinel roles granted:
- Sentinel Contributor
- Microsoft Metrics Publisher
- Microsoft preview community (optional) to get access to support and resources.
Get support
If you need assistance with connecting Knox Asset Intelligence to your Microsoft Sentinel environment, please submit a support ticket. In the Subject line, ensure that you mention “Microsoft Sentinel” so our team can respond to your issue accordingly.
On this page
Is this page helpful?